TLS
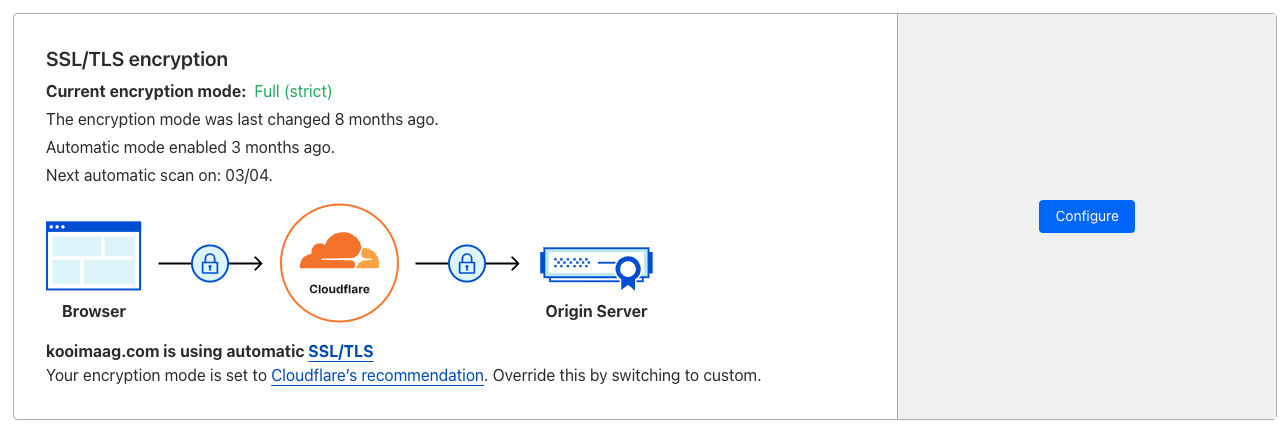
When using CloudFlare for Proxied DNS, we want to ensure that the connection from CloudFlare to our server is encrypted.
When possible, we prefer Full (strict) mode.
Resources used
Steps to implement strict mode
TODO when I set this up on a server again.
Testing a site configured with an Edge Certificate
When adding a CloudFlare edge certificate to a site, it can be tricky to run the curl command against that site from the command line on the server. This is generally due to the certificate essentially being a "self-signed" certificate.
It's perfect to use and is trusted by CloudFlare. But there's no public trusted chain associated with it.
To get around, this it's possible to tell curl how to work with the certificate correctly.
A regular curl command would look like this and would likely fail:
forge@<server>:~$ curl -k --resolve www.ktparts.com:443:127.0.0.1 https://localhost
curl: (35) OpenSSL/3.0.13: error:0A000458:SSL routines::tlsv1 unrecognized name
Here, even with the -k flag, curl is unable to verify the certificate. This is because the certificate is associated with a specific host name.
We can tell curl how to resolve the host correctly, but spoofing the request to the correct host name.
forge@<server>:~$ curl -k --resolve www.my-site.com:443:127.0.0.1 https://www.my-site.com
Here, we're telling curl that any request to www.my-site.com should be resolved to 127.0.0.1 on port 443.
The -k flag tells curl to ignore the certificate verification errors which it would still have because it's not a public trusted certificate.